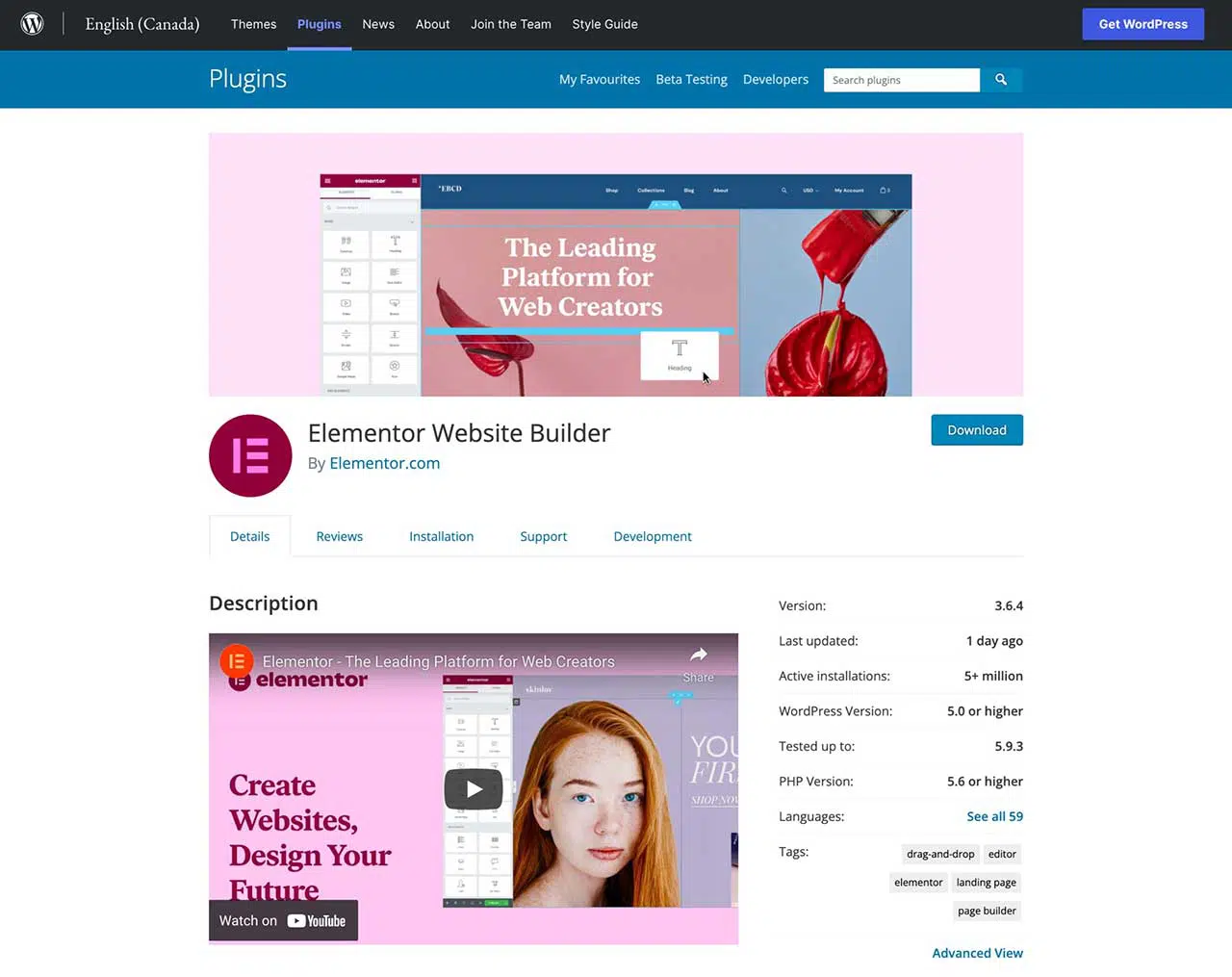
Heads up, Elementor users! The Wordfence Threat Intelligence team discovered a critical vulnerability in the popular Elementor plugin for WordPress with over 5 million installs. The vulnerability allowed any authenticated user to upload arbitrary PHP code.
The Wordfence team sent out disclosure to the folks at Elementor on March 29th and April 5th. But because they did not receive any response from them, they forwarded the disclosure to the WordPress plugins team leading to the release of a patched version of the plugin, Elementor version 3.6.3 released on April 12th.
Here are some details from the Wordfence blog:
The Elementor plugin for WordPress introduced an Onboarding module in version 3.6.0, designed to simplify the initial setup of the plugin. The module uses an unusual method to register AJAX actions, adding an
Wordfence Official Blogadmin_initlistener in its constructor that first checks whether or not a request was to the AJAX endpoint and contains a valid nonce before calling themaybe_handle_ajaxfunction.
Unfortunately no capability checks were used in the vulnerable versions. There are a number of ways for an authenticated user to obtain the
Wordfence Official BlogAjax::NONCE_KEY, but one of the simplest ways is to view the source of the admin dashboard as a logged-in user, as it is present for all authenticated users, even for subscriber-level users.
Aside from what was mentioned above, the vulnerability also allowed any logged-in user to use any of the onboarding functions. Also, a malicious attacker could create a fake “Elementor Pro” plugin zip file and use the upload_and_install_pro function to install it. Any code contained in that fake plugin would be executed and used to take over the site or gain access to additional resources on the sites’ web server.
A less severe vulnerability using the maybe_update_site_name, maybe_upload_logo_image, and maybe_update_site_logo functions enable a malicious attacker to deface the site and change the site’s name and/or logo.
For more details on the critical vulnerability, please check out the official Wordfence blog.
If you are using Elementor on your site or client sites, upgrade the plugin ASAP! If you don’t check your WordPress site regularly, I recommend that you enable automatic updates to make sure that any vulnerable plugins are kept up to date.
Hats off to the folks at Wordfence, especially their Threat Intelligence team for disclosing the vulnerability and to the WordPress plugins team for releasing a patched version of the Elementor plugin.