Just found out from Weblog Tools Collection about a certain website with the name WordPresz.org that pretended to be WordPress.org and tried to release a backdoored (trojanised) version of WordPress to unsuspecting users who are still using older versions of the popular blogging platform. Blogger Craig Murphy was the first to report about this issue and below is a summary of his report taken from Sophos.com.
“Craig talks about how when he logged in to his admin account in WordPress he received a “High Risk Vulnerability Warning” from a spoofed WordPress domain. (The last ’s’ in WordPress.org has been replaced by a ‘z’.) The Warning suggests upgrading to the ‘new’ version 2.6.4 of WordPress. Downloading this ‘new’ version of WordPress I found that of the 638 files in version 2.6.4, 637 were identical to the same files in the official 2.6.3. The only difference was in the file pluggable.php. The hacked version of the file pluggable appears to be stealing the content of cookies on larger installations of WordPress. Sophos are now detecting this file as Troj/WPHack-A.”
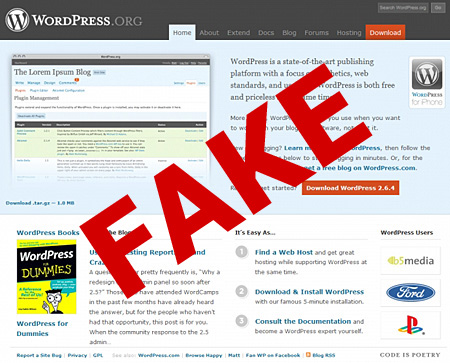
WordPresz.org, setup by malicious persons was designed to steal valuable information stored in cookies from users who install the compromised version of WordPress and could also potentially be used to hijack these WordPress installations for malicious purposes. WordPresz.org is no longer online but the site looks exactly the same as the real thing. Below is a screenshot of the fake site.
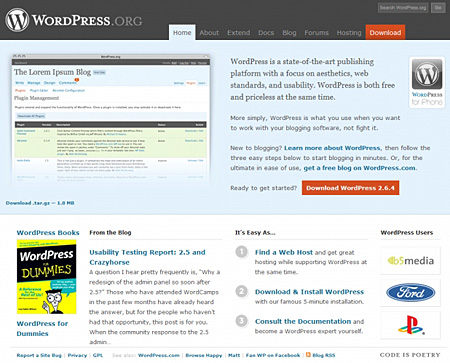
If you can’t see the difference, below is a screenshot made by Craig pointing out the differences between the real and the fake WordPress site.
1 – the download size is too round and is incorrect, it should be about 1.4mb in this case.
2 – these are randomised over at WordPress.org, but are static at WordPresz.org.
3 – The real WordPress.org has a “Showcase” link included.
It’s really hard to know the difference between the two sites and any WordPress user could be lead to believe that they’re visiting the real one.
Here’s Peter Westwood’s (one of WordPress’s lead developers) response to this incident:
It looks like sites which have not upgraded to 2.6.3 are being exploited in an interesting way whereby a hacker, probably using an automated script, is hacking into sites with the vulnerability and changing the settings of one of the dashboard modules to point to a different feed thereby encouraging people to go to a different site which is offering a dodgy upgrade.
“We recommend that people upgrade as soon as possible when we release a security release so as to ensure they are not vulnerable to issues which will likely have exploits in the wild.
Also in the upcoming 2.7 release of WordPress we are including a built-in upgrade mechanism within WordPress which will allow people to upgrade automatically with ease. I would however stress the need with any piece of software to check that an upgrade is real by visiting the website of the software provider manually rather than relying on a link that you have been provided. Otherwise, as with bank phishing scams there is the potential for someone to trick you into doing something you didn’t want to do.
This is not the first time hackers and fraudsters tried to released compromised version of WordPress. Early last year, I published WordPress 2.1.1 – Dangerous Download, which is about how crackers were able to upload a backdoored version of WordPress 2.1.1 into one of the servers powering WordPress.org. Other instances include websites trying to distribute WordPress themes containing malicious codes.
These is another good reminder for all of us WordPress users to practice safe computing. For those of you who are still using an old version of WordPress, please take the time to upgrade to the newest version. Make sure you update your WordPress installation to the most recent version especially if the newer version contains a security fix. Also, make sure that you download your next WordPress install ONLY from WordPress.org and not from any other site. Users should also be careful what themes and plugins you download/install and where you get it from. As much as possible download only from WordPress Extend or from reputable plugin and theme authors.
To those of you who think that you’ve been victimized by WordPresz.org and believe that your WordPress installation has been compromised, download the newest version or WordPress from WordPress.org and do a reinstall/upgrade.
To know more about the details of this story you can visit the following links:
- Craig Murphy – WordPress 2.6.4 Fake?
- The Register – Fake site punts Trojanised WordPress
- ZDNet Blogs – Fake WordPress Site distributing backdoored release
Any of you guys were able to visit the actual fake WordPress site? Anyone had the same experience as Craig Murphy? What other security and safety measures can you suggest for other WordPress users to make sure they keep their blogs clean and safe? Please share your thoughts. Thanks for your time!
*images taken from The Social Programmer and ZDNet Blogs.










@Tom – Very sneaky indeed! :D
That is so sneaky!
@Gachinpo – I’m not sure if anyone knows the identity of the persons behind this fake website. But whoever they were, they planned to use the site to install the backdoored version of WordPress to gather information from compromised blogs and maybe hijack it too. It could also be used to do other malicious activities without the blog owner knowing it.
You’re welcome! Although this fake website is now offline, I posted about this so more WordPress users would be aware of these type of things and be more careful next time.
Thanks for dropping by!
Who made this fake WordPress.org site?! What’s on his mind about doing this..
Thanks for posting this one, many might have been fooled with this fake site.
@Jamie – You’re most welcome! The reason why I publish these posts is to help spread the word and make other WP users aware of these kind of things. It really helps to be cautious and playing it safe. :)
Thank you for the heads up JayPee. I would have never thought about double checking a site where I thought it would be safe. Since you pointed out the “title” segment, I am a little bit more cautious with all the sites I upgrade.
@Ant – For me, it’s surprising but not shocking. This has to be expected as WordPress has become more and more popular and having millions of users. WordPress users have to be very careful and vigilant against these types of things.
Yeah, it’s good that this was uncovered soon and the site was brought down quickly after that.
That’s shocking! I’ve never seen WordPress mimics being used in a phishing scheme such as how PayPal mimics are used. Glad the site is currently in a down state.
@Ambo – That’s good. Me, I do the upgrade manually and get the latest version from the real WordPress website. Btw, you won’t need that plugin when WP 2.7 is released because of the automatic upgrade feature.
You’re welcome bro and have a good weekend! :)
Thank God i am using WordPress Automatic plugin. This site is very alarming. Thanks for sharing bro.
@Riyanne – I’m sure no one does, except for the people who are behind them. These people are not only guilty of copyright infringement but they can be considered criminals because they were trying to distribute a trojan-filled installer which they can use to gather data and personal information from compromised blogs.
I really don’t like misleading sites or misleading keywords.
I think they could get sued
@loy – That’s correct. Although even experienced WP users could get fooled if they’re careless and do stuff in a hurry.
Regarding the automatic upgrade feature, it will be one of the features added to WordPress 2.7 which will be released soon.
Thanks for dropping by and sharing your thoughts! :)
The name and the URL themselves look malicious enough. But WordPress newbies can be fooled.
The problem is that WordPress doesn’t have an in-built automatic upgrading feature (a plugin exists for that but I haven’t tried it. I’m still in WordPress 2.6.2). This forces WordPress users to visit the website to try and download the latest version. One small mistake in typing (wordpresz instead of wordpress) and oopss… the unknowing person downloads the fake WordPress.
@Ade – Me too, until I read the whole story.
Whoa. I didn’t know it was THAT serious.
@rhoen – You’re welcome kuya! Yes, its always good to practice safe computing. :)
thanks for heads-up, jaypee! this sure helps to be very careful!